Hackers are abusing Googlebot servers to deliver malicious payloads.
Last year, HackRead exclusively reported on how hackers were using Google Adwords and Google Sites to spread malware. Then came another shocking research from Cisco Talos exposing how hackers exploited Google Search Results to distribute Zeus Panda banking trojan.
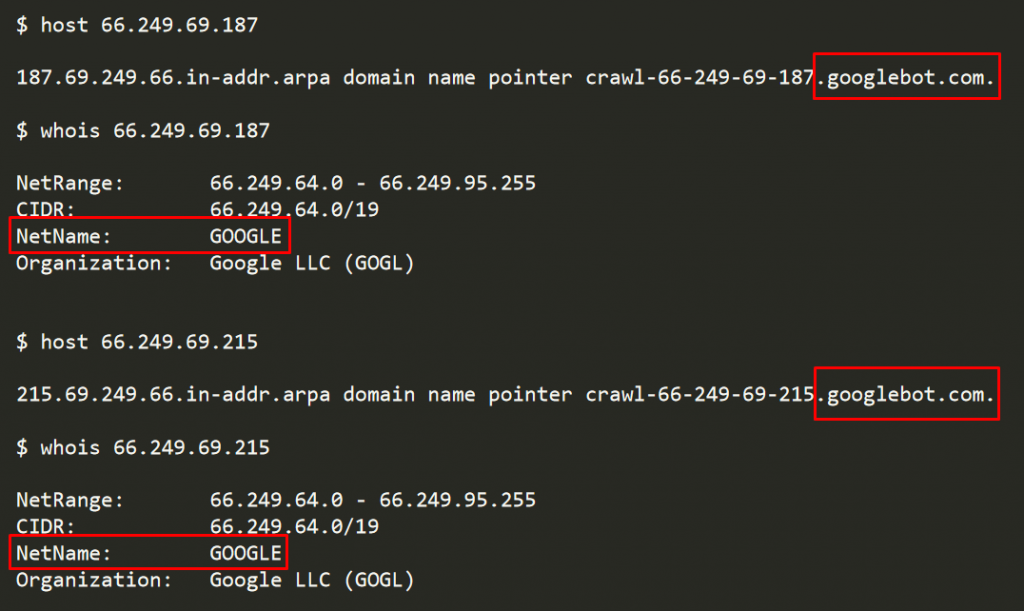
Now, researchers at F5 identified a strange and infrequent behavior at Googlebot servers where malicious requests were originating from them. This poses serious consequences because many vendors trust Googlebot to such an extent that they let them influence their organizational security decisions.
The malicious requests were being received at the F5 threat intelligence system from legitimate Googlebot servers. Presumably, an attacker was deliberately doing so either by gaining control of the Googlebot server, which was quite unlikely, or by sending a fake User-Agent via some other Google service, such as, Google Sites.
However, researchers believe that the requests were originating from the subdomain of Googlebot and its IP address pool instead of another Google service. Hence, they came to the conclusion that Googlebot was being exploited.
The remote code execution flaw (CVE-2018-11776) identified in Apache Struts 2 in August this year delivered JavaPayload through the URL; F5 researchers noticed that the CroniX campaign exploited it to distribute crypto-mining malware. The same threat actor was being used to exploit Googlebot service. Interestingly, researchers noted, some of the offending requests generated in CroniX campaign actually originated from Google servers.
It must be noted that trusting Googlebot is compulsory if you want your website to appear in Google’s search engine results. Therefore, a majority of vendors simply trust the legitimacy of the traffic that comes via Googlebot servers. This implies that it was possible for malicious requests originating from Googlebot servers to bypass some of the key security mechanisms without any authentication and may end up delivering malicious payloads. If these IP addresses are automatically blocked by an organization’s mitigation mechanism, Googlebot will be blocked and this would lower the organization’s ranking on Google.
Basically, Googlebot follows every link, whether new or updated one, on your site and follows the link from these pages to let Google add previously unknown pages to expand its search engine database. This method also lets Google analyze new websites before making them available to users. This method involves sending a GET request to every URL that the links contain. Googlebot’s generated requests are based on the links that they have no control over and such links are never validated.
This method can be exploited easily by attackers by tricking Googlebot into sending malicious requests to random targets; they can add such links on a website and each of the links will contain target’s address and attack payload already. Such a link may look like this: hxxp://victim-address.com/exploit-payload
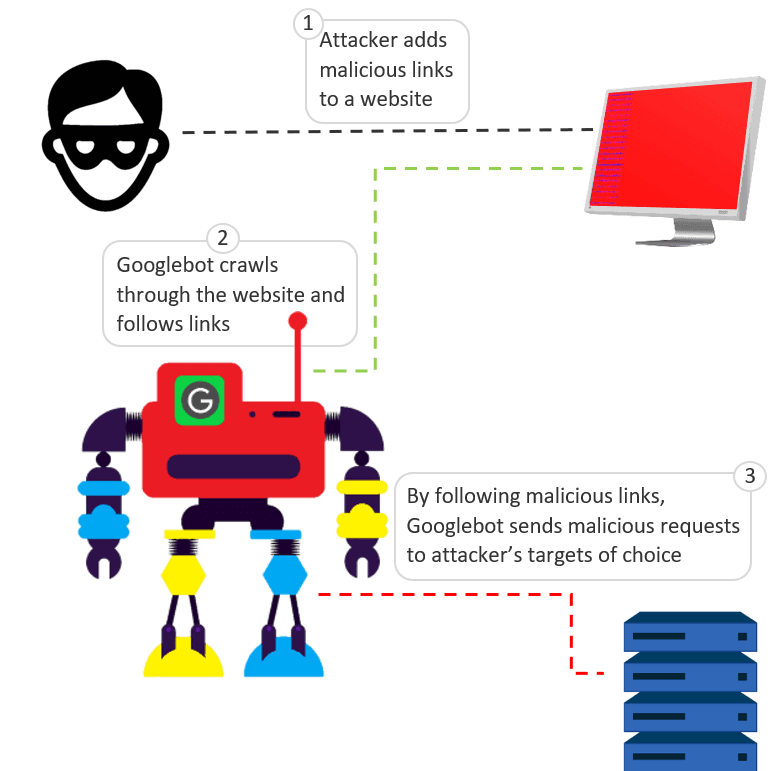
When Googlebot will identify this link (victim-address.com), it will follow it and send a malicious GET request to the targeted address, and the request will hold the exploit-payload. F5 researchers checked the method by manipulating Googlebot to send malicious requests to a targeted IP address using two servers, one for the attacker and the other for the target.
Furthermore, through Google Search Console, researchers configured Googlebot to obtain the link from the attacker’s server that held a malicious payload and after some time they could see the malicious request hit the target server. This proved that the request was generated from an authentic Googlebot server.
It is worth noting that attacker can only control the malicious request URL and cannot modify HTTP headers, GET request method and the payload. Moreover, the attacker can’t track responses to the malicious requests and Googlebot will decide the delivering time of the malicious request.
It is advised that vendors should recheck their trust level in relation to third-party services to ensure that there are multiple levels of security, and sent data should be validated. F5 has reported the issue to Google and the company has acknowledged the bug as well. Let’s see how long does it take Google to fix this issue.