A technical paper titled “EarSpy: Spying Caller Speech and Identity through Tiny Vibrations of Smartphone Ear Speakers” has revealed how snoopers can exploit motion sensors installed inside Android cellphones can help adversaries eavesdrop on the user’s conversations.
Startling Facts About Motion Sensors
A team of researchers from different universities, including Rutgers University, Texas A&M University, Temple University, New Jersey Institute of Technology, and the University of Dayton, conducted the research.
The research team comprised Ahmed Tanvir Mahdad, Cong Shi, Zhengkun Ye, Tianming Zhao, Yan Wang, Yingying Chen, and Nitesh Saxena.
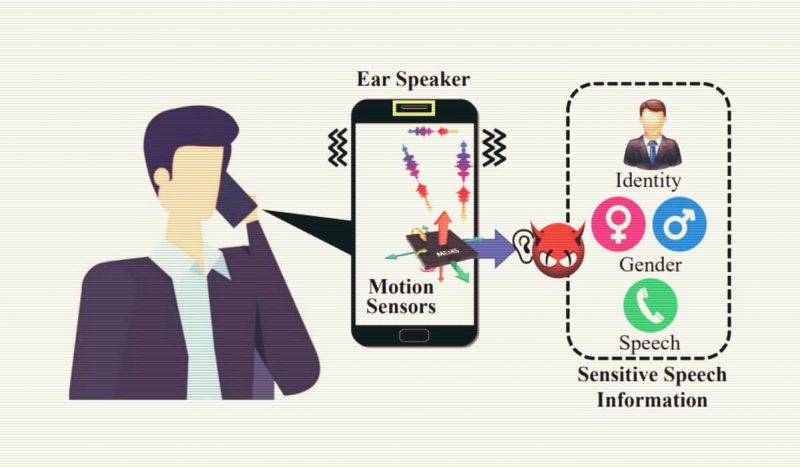
Dubbing this side-channel attack EarSpy, researchers noted that motion sensors could be used for registering ear speaker reverberations so that the attacker can determine caller identity and gender and listen to their private conversations.
This research has substantiated the assumption that eavesdropping through capturing motion sensor data is possible.
How does EarSpy Attack help in Snooping?
Researchers wrote that the study (PDF) was based on the belief that smartphones’ built-in motion sensors can let attackers collect data on indoor locations and touchscreen inputs along with listening to audio conversations without needing explicit permissions before collecting raw data.
Initially, they thought generating powerful vibrations through ear speakers to eavesdrop on user conversations wasn’t possible. But during their research, the team realized that modern smartphones have high-quality stereo speakers and highly sensitive sensors that can detect finer vibrations.
Hence, they finally determined the ideal environment for successful eavesdropping using various devices and techniques. They used multiple pre-recorded audio files, a 3rd party application for capturing sensor data as they simulated calls, and a machine learning algorithm for results interpretation.
Research Findings
The team found that gender detection was 98.6%, and speaker detection was up to 92.6% accurate. Moreover, they found speech detection up to 56.42% accurate. This proved the existence of differentiating between speech features in the accelerometer data that attackers can exploit for spying. EarSpy focused on gender recognition using data collected at 20 Hz, which indicates a lower sampling rate can allow attackers to determine the user’s gender.
How to Prevent Eavesdropping?
Researchers recommended limiting permissions to counter eavesdropping via sensor data so that 3rd party applications cannot record sensor data without the user’s permission. It is worth noting that Android 13 doesn’t allow sensor data collection at 200 Hz without the user’s permission to prevent accidental data leaks.
Furthermore, experts suggested that mobile device manufacturers must be cautious about designing more powerful speakers and instead focus on maintaining a similar sound pressure during audio conversations as was maintained by old-generation phones ear speakers.
Lastly, positioning motion sensors as far from the ear speaker as possible could minimize the phone speaker’s vibrations and diminish spying chances.