ProofPoint researchers released a report on Tuesday, which revealed that cybercriminals are now hijacking the Brazilian internet connections by altering their DNS (domain name system) settings. These kinds of attacks are termed as pharming attacks.
Pharming Attakcs:
Pharming attacks are designed to attract victims towards fake websites. These fake websites are usually replicas of banks and are used to steal credentials and similar sensitive data.
Usually, pharming attacks are highly efficient and in majority of the cases these cannot be spotted. By changing the DNS settings of the routers, hackers ensure that victims are redirected to a fake website as soon as they type-in the domain name of the real or legitimate website in the address bar of their web browser.
Related Post: ASUS routers can be easily hacked due to vulnerable firmware
ProofPoint Study:
It was previously assumed that only in network-oriented attacks can the DNS be hijacked but recent attacks show that phishing emails can prove to be just as effective.
Proofpoint researchers started monitoring this operation from December 2014 onwards and as per their observations the attacks began with the emergence of a spam email sent from one of the leading telecomm companies of Brazil.
Related Post: 16Mn Devices Compromised by Sophisticated Mobile Malware: Study
The security company observed a small spam run over a four-week period in which no more than 100 emails were sent out specifically to Brazilian organizations and users.
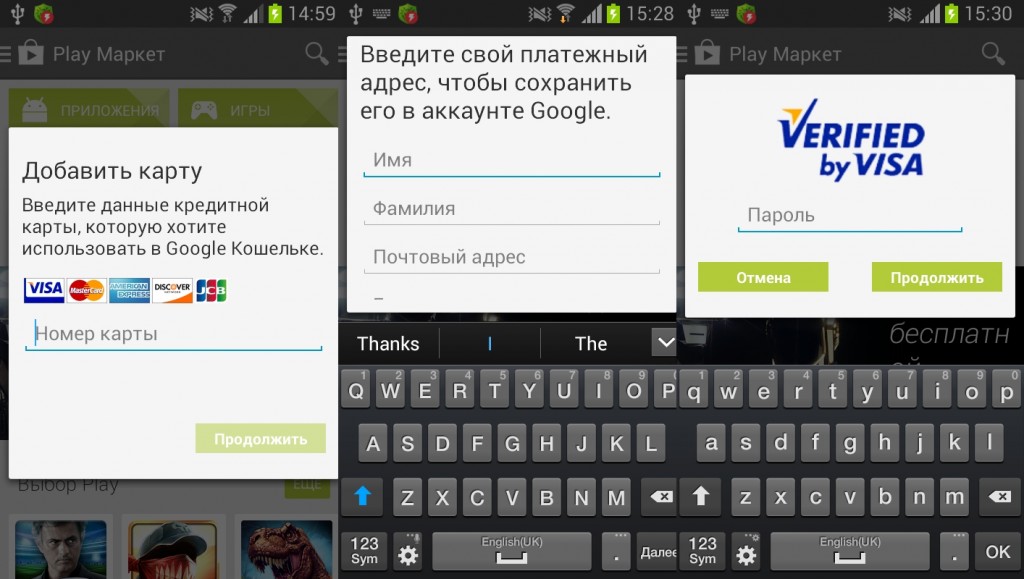
These emails contained links pointing to a webpage. This page was hosting malicious iframes, which were designed to abuse cross-site request forgery (CSRF) vulnerabilities that are usually present in the UTStarcom and TP-Link home routers.
The device manager’s login page was brute forced by a malicious code when common IP addresses and default passwords were tried out.
After compromising the administration page, the IP address for the router’s primary DNS server was also replaced with a malicious DNS IP.
Such attacks against users in Brazil were recorded by Kaspersky researchers in September 2014 too. However, it is evident that afterwards, the cybercriminals stepped-up their mechanisms.
Previously, both the primary and secondary DNS records were modified by the hackers but in recent such attacks, it has been observed that hackers only changed the Primary DNS server with their malicious server and then the secondary DNS was set to Google’s public DNS 8.8.8.8.
This helped hackers in resolving DNS requests from compromised devices if the malicious server wasn’t available and this technique is highly difficult for victims to suspect.
Pharming attacks are efficient since there is no need to take over a public DNS. If victims try to access any of the hacked websites, the request gets processed via the rogue DNS server and the victims are immediately taken to the compromised page.
Related Post: Hacker Maps Internet by Enslaving Thousands of Vulnerable Machines
This aspect was explained in detail by proofpoint researchers in a blog post:
“ could be used to intercept and tamper with email communications, web sites, logins and passwords and other confidential or sensitive information, software downloads, hijack search results, redirect to a TDS and malware, and other malicious actions.”
The reason why home-based routers become easy targets of hackers is that many such devices are vulnerable to threats for instance, the Misfortune Cookie bug that was recently discovered and exposed millions of SOHO routers. Follow @HackRead