Microsoft acknowledged the incident and currently investigating the issue but at the same time downplaying its impact.
In recent news, it has been found that Microsoft signed off a third-party driver, Netfilter, for Windows that contains rootkit malware and has been circulating mainly amongst the gaming community.
This was first found out by Karsten Hahn, a G Data malware analyst, who tweeted about this after noticing the “Netfilter” which he later traced, analyzed, and identified as bearing Microsoft’s seal.
New article: Microsoft signed a malicious Netfilter rootkit
Thanks for your contributions @jaydinbas @cyb3rops @cci_forensicshttps://t.co/6mtxONK1YS
— Karsten Hahn (@struppigel) June 25, 2021
When Microsoft observed the rootkit, it was found out that it communicated with Chinese command-and-control IPs (C2) and as it turns out, these belong to one of the companies that the United States Department of Defense labeled as “Community Chinese Military”.
The driver maker, Ningbo Zhuo Zhi Innovation Network Technology, was working with Microsoft to study and patch any known security holes, including for affected hardware. Users will get clean drivers through Windows Update.
Although Microsoft admitted its mistake and started investigating the incident, they did downplay the impact of the driver. They focused on the idea that since the driver was aimed at gamers and only circulated in the gaming community, it isn’t known to have compromised any enterprise users.
Moreover, they added that the rootkit only works if a user authorizes the driver and it obtains administrator-level access on a PC to install the driver. The idea is that Netfilter won’t pose a threat to your PC unless you go out of your way to install it.
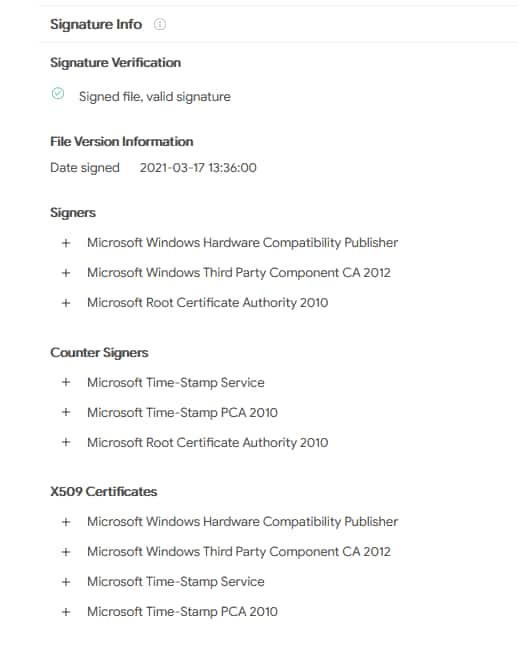
In a blog post, Microsoft said it would be “refining” the signing process, partner access policies, and validation. The tech giant announced that it has already suspended the account and is now being reviewed to submit added malware signs.
We have seen no evidence that the WHCP signing certificate was exposed. The infrastructure was not compromised, Microsoft said.
The actor’s activity is limited to the gaming sector specifically in China and does not appear to target enterprise environments. We are not attributing this to a nation-state actor at this time, the company revealed.
The actor’s goal is to use the driver to spoof their geo-location to cheat the system and play from anywhere. The malware enables them to gain an advantage in games and possibly exploit other players by compromising their accounts through common tools like keyloggers, warned Microsoft.
Nevertheless, the incident isn’t entirely comforting. Many people see a signed driver as confirming that a driver or program is safe. Those users might be hesitant to install new drivers in a timely fashion if they’re worried there might be malware, even if those drivers come straight from the manufacturer.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.