The hack attack took place due to the classic Magecart attack in which “skimmers” are used to steal payment data.
Recently, Claire, a Jewelry, Accessories & Toys retail giant based in the US temporarily closed all of its physical stores numbering well above 3000, including that of a subsidiary named Icing. Done on March 2020 in response to COVID-19; it then shifted its focus to operating via online stores hosted on Salesforce Commerce Cloud.
However, according to a report by researchers from Sansec, this didn’t fare well resulting in the site being hacked due to the classic Magecart attack in which “skimmers” are used to steal payment data.
What happened
How this happened can be traced to the very next day of when the stores closed down – on the 21st of March 2020 when attackers registered a domain named <claires-assets com> anonymously using Namecheap.
See: How to check for websites hacked to run web skimming, magecart attack
Although no foul play was observed through this for about a month, later on, April 25, a malicious piece of code was finally injected to both Claire’s and Icing’s website designed to steal customer payment data during the checkout process.
The stolen data would then be sent to the attacker-controlled domain allowing them to have access to the information.
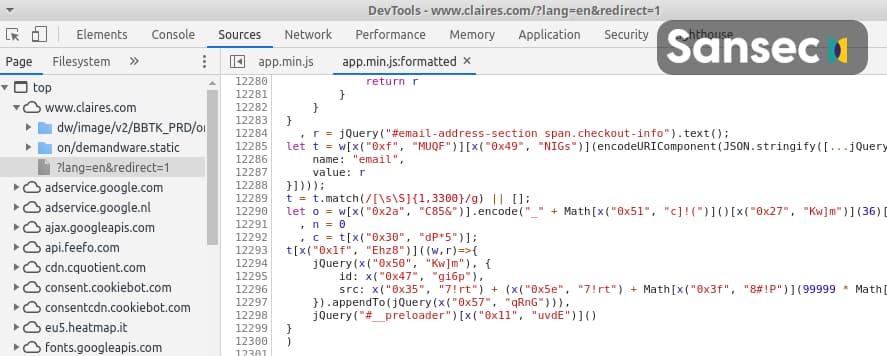
Considering that the malware was found within the above file, the researchers believed that as “this file is hosted on the store servers, so there is no ‘Supply Chain Attack‘ involved, and attackers have actually gained write access to the store code.”
This, therefore, absolves Salesforce of any responsibility as they do not happen to be the cause here. Elaborating further on how users were lured into the attack, Sansec stated in a blog post that,
The skimmer attaches to the submit button of the checkout form. Upon clicking, the full “Demandware Checkout Form” is grabbed, serialized and base64 encoded. A temporary image is added to the DOM with the _preloader identifier.
The image is located on the server as controlled by the attacker. Because all of the customer submitted data is appended to the image address, the attacker now has received the full payload. Immediately, the image element is removed.
Currently, thankfully though, the malware has been removed by Claire after being notified by the researchers. As for the measures the company is taking to reduce any such future occurrences, the management was reported as saying,
We are working diligently to determine the transactions that were involved so that we can notify those individuals. Cards used in our retail stores were not affected by this issue. We have also notified the payment card networks and law enforcement. It is always advisable for cardholders to monitor their account statements for unauthorized charges. The payment card network rules generally provide that cardholders are not responsible for unauthorized charges that are timely reported.
To conclude, it is probable that the attack’s planning took place during the 4 weeks between the attack and when the aforementioned domain name was registered by the attackers.
Even though the cause of how such a vulnerability was made exploitable has not been revealed, possible ones include a spearphishing campaign by the attackers, password leaks of the administration, and a flaw in the company’s internal networks.
In a conversation with Hackread.com, Raif Mehmet, Bitglass’ VP for EMEA region said that,
“Payment card-skimming malware continues to be a security challenge for retailers around the globe. British Airways, Newegg, and now Claire’s have all been victims of Magecart’s malware, highlighting the need for security solutions that monitor for vulnerabilities and threats, across all devices and applications, in real-time. With these capabilities, retailers can be proactive in detecting and thwarting breaches before they happen, ensuring that their customers’ sensitive information is protected.”
See: VisionDirect hacked: Hackers infect domains with malicious Google Analytics code
Nonetheless, Claire should use this opportunity to do good on their promise and step up their security practices such as hiring an external pen-testing security team. Customers on the other hand should pay attention to the company’s advice and review their credit/debit card statements immediately.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.