The attack puts personal and financial data of millions of people at risk.
Local governments across the United States have been firefighting on several different fronts as a result of the Coronavirus pandemic. This has also involved cyberattacks including the one on the Department of Health and Human Services (HHS) in March this year.
But, this time the websites of 8 cities across 3 states in the US have been hacked with credit card skimmers in a classical Magecart attack. This attack allowed attackers to steal the payment information of all citizens using the website. But how crucial is it?
See: Attackers steal payment information through Google Analytics
Turns out to a wider extent. You see, all of these websites are built on the Click2Gov platform which allows local governments to provide vital services such as the payment of utilities, complaint management, and community engagement. Therefore, most residents would naturally be using them increasing the victim net.
This is because the general perception is that government websites are “naturally secure” just like Android users believing in Google and downloading malware-infected apps from Play Store as if it’s a secure platform after all Google owns it.
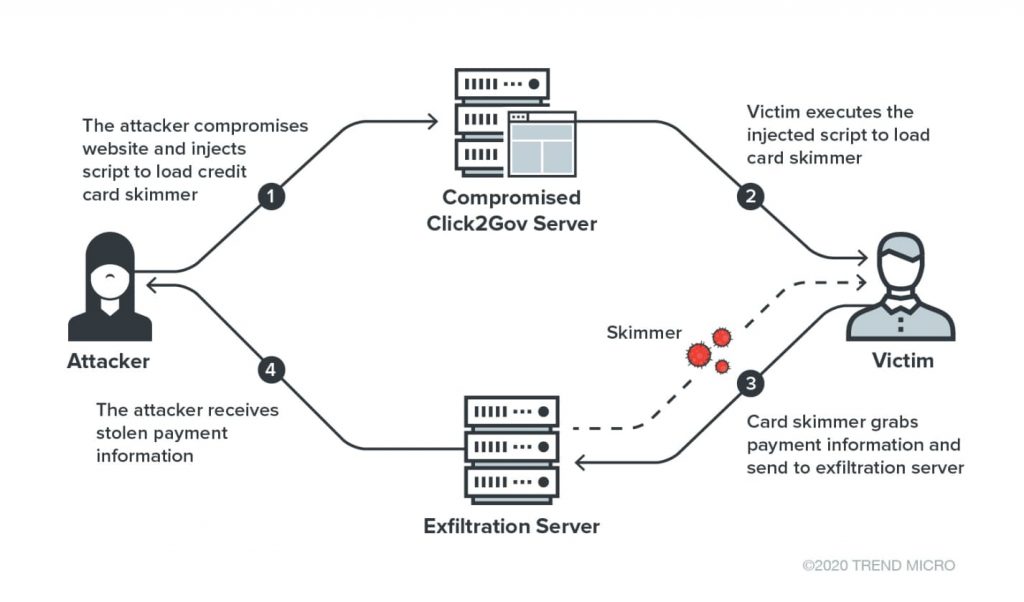
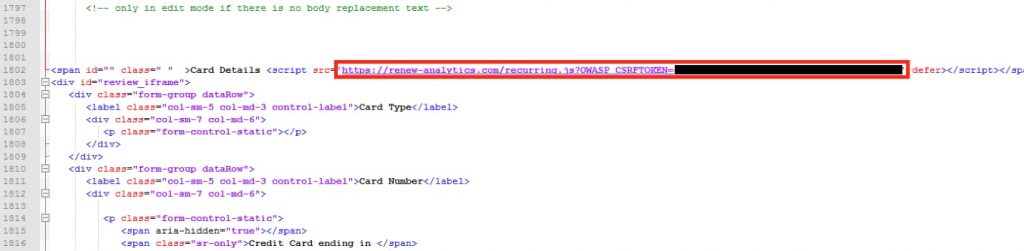
The attack took place through the process shown in the above diagram with a piece of Javascript code being used for the infection itself on the payment page.
Explaining further, Joseph C Chen, Trend Micro’s fraud researcher wrote in a blog post that,
Unlike other skimmers which grab data on various types of payment forms, the skimmer used here is rather simple and only works on a Click2Gov payment form. No obfuscation or anti-debugging techniques were used.
On the other hand, the exfiltration servers to which the collected data was transmitted consisted of 2 separate servers with 1 being used for 3 sites and the other for the remaining 5. Both though hosted the same set of files involving the skimmer – it may be that their separate use was to diversify the risk of getting caught.
Coming to the leaked data, due to the sensitive nature of the site, as already mentioned, both personally identifiable information such as names and contact addresses were extracted along with the payment details entered by residents on the web portals.
See: How to check for websites hacked to run web skimming, magecart attack
Therefore, citizens should be immediately notified so they can take precautionary measures such as changing their credit card details and being on the lookout for phishing and spam campaigns.
To conclude, this is not the first time that these websites have been compromised. Previously in 2018 and 2019, we’ve seen similar incidents occurring and so the only way to rectify this situation is to demand greater security measures from the developers of the site.
Otherwise, we will continue seeing such security breaches placing Americans at a risk that is hideous but dangerous in the long term.
Moreover, on a general note, due to the rise in skimming attacks, authorities are advised to pay greater attention to the security of their website’s payment pages specifically as they happen to be the easiest target for malicious actors.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.