Currently, DotRunpeX malware appears to be primarily distributed through phishing emails and malicious Google Ads, presenting a significant threat to users’ systems.
A new malware that distributes multiple known malware families, including Agent Tesla, FormBook, Ave Maria, NetWire, LokiBot, Raccoon Stealer, Remcos, RedLine Stealer, Vidar, and Rhadamanthys, has been discovered by Checkpoint researchers.
Dubbed DotRunpeX, the malware is a new injector written in .NET, created using the Process Hollowing technique, and used to infect systems with different malware families.
The researchers noted that DotRunpeX is being actively developed. Its infection chain invades the system as a second-stage malware, usually deployed via a downloader or loader delivered via malicious attachments in phishing emails.
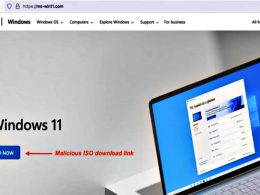
Additionally, it can leverage malicious Google Ads that appear in search results to direct unsuspecting users when they search for commonly used software such as LastPass and AnyDesk and send them to copycat sites delivering trojanized installers.
Though the injector is fairly new, there are several similarities it shares with its previous versions. For example, the injector’s name is derived from its version information, which is the same for both versions across all samples the researchers analyzed. They also noted that it contained ProductName – RunpeX.Stub.Framework.
Their analysis revealed that each malware sample had an embedded payload of a specific malware family to be injected, which becomes possible by abusing the vulnerable procexp.sys process explorer driver incorporated into the malware for obtaining kernel mode execution.
They analyzed publicly shared data by independent researchers regarding DotRunpeX but learned that the malware was misattributed to a well-known malware family. Furthermore, they learned that the first-stage loader and the second-stage loader had no connection.
The most recent activity of DotRunpeX was detected in October 2022. It was noticed that using the KoiVM virtualizing protector adds an extra obfuscation layer. These findings were somewhat similar to a malvertising campaign discovered by SentinelOne in February 2023. In that instance, the loader and injector components were referred to as MalVirt.
Researchers suspect that the malware may be operated by Russian-speaking groups, given the references to the language in its code.
RELATED NEWS
- New YTStealer Malware is Hijacking YouTube Channels
- YouTube Tutorial Videos Spread Vidar, Raccoon Malware
- Adsense abused: 11,000 sites hacked in a backdoor attack
- Google Drive behind most malicious Office doc downloads
- Google Ads drop FatalRAT in fake messenger, browser apps