The total number of impacted Android apps’ users is around 24,000.
With the rise of smartphone adaptation in the previous decade, a range of tools were developed to aid developers in building apps. One such tool happens to be Firebase, a Google-owned development platform used by over 1.5 million apps representing 30% of all apps on the Play Store.
It is used to provide various functions such as cloud storage, A/B testing, analytics, and even predictive capabilities. In relation to it, a couple of days ago, Comparitech, a security firm has come up with an alarming revelation detailing that up to 24000 Android apps may be at risk because of certain misconfiguration on the databases stored on the platform.
These can allow threat actors to gain access to the personal data of the users of these apps along with access tokens which can enable unauthorized logins.
See: Welp – Google sent your photos & videos to strangers
The misconfiguration allows an attacker to add “.json to the end of a Firebase URL” and hence view all the content contained within the database with the help of simple search engine search results.
An example is “https://.firebaseio(dot)com/.json” as elaborated by the researchers. Further, they state, “If the database is publicly exposed, this request will return the full contents of the database. Otherwise, it returns an “access denied” message.” These results though are not possible on Google itself as they stopped displaying them back in December 2019, but they are still available on Bing.
Commenting in their blog post on how the researchers came up with the number of apps affected, they state:
Comparitech’s security research team led by Bob Diachenko examined 515,735 Android apps, which comprise about 18 percent of all apps on Google Play.
In that sample, we found more than 4,282 apps leaking sensitive information. If we extrapolate those figures, an estimated 0.83 percent of all Android apps on Google Play leak sensitive data through Firebase. That’s roughly 24,000 apps in total.
However, since Firebase also supports other platforms such as iOS, it does not mean that only Android apps are at risk, other developers should also pay heed.
Delving into the specifics of the data at risk, the researchers state that these 24000 apps have been installed approximately 4.22 billion times which by every measure is a huge number.
Further, since the average apps that a user installs ranges well above 60, there are high chances that a user’s data may have been compromised because of anyone app if not all of the installed ones.
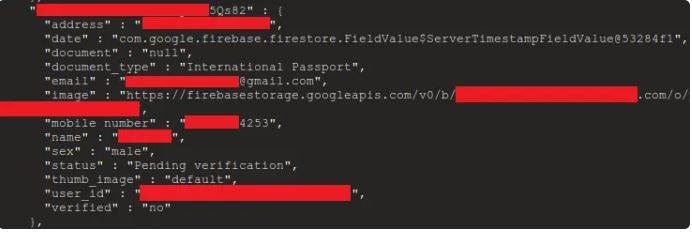
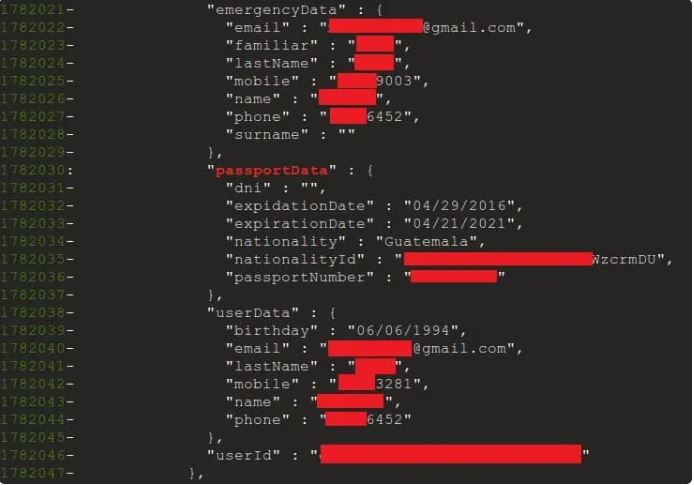
The personal data can be divided into the following record-wise:
- E-mail addresses: 7,000,000+
- Usernames: 4,400,000+
- Passwords: 1,000,000+
- Phone numbers: 5,300,000+
- Full Name: 18,300,000+
- Chat messages: 6,800,000+
- GPS data: 6,200,000+
- IP addresses: 156,000+
- Street addresses: 560,000+
- Credit card numbers
- Government-issued identification such as passports
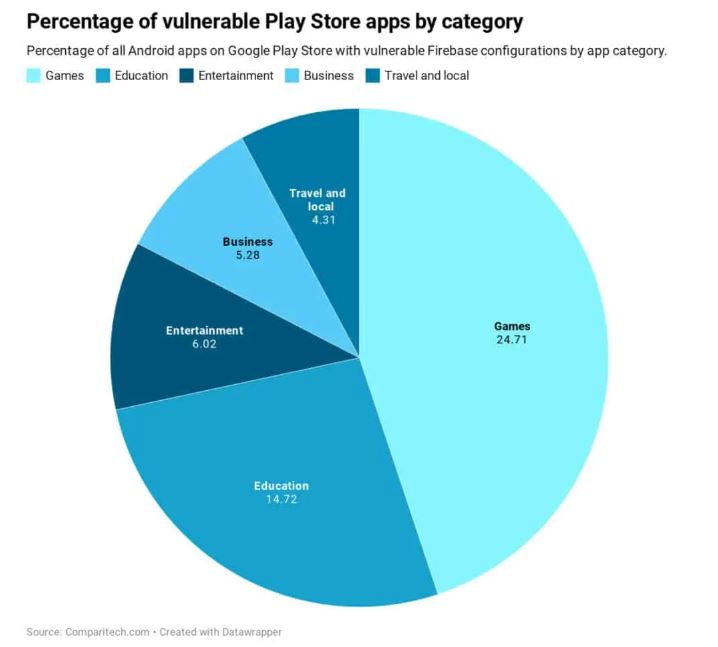
The categories of the apps exposed are as follows with games making up the majority:
Another major revelation was that amongst the apps analyzed, 11,730 of them had databases exposed to the public out of which 9,014 allowed unauthorized personnel to make edits to the database including adding, deleting, and modifying the data.
See: 500 Google Chrome extensions found to be spreading malware
These could hence be used to redirect users to malicious websites by attempting phishing, populating the apps with fake data to misguide users, and even corrupt all the data leading to a loss of the entire database.
To conclude, these findings were reported to Google on April 22 to which they have positively responding stating the following:
Firebase provides a number of features that help our developers configure their deployments securely. We provide notifications to developers about potential misconfigurations in their deployments and offer recommendations for correcting them. We are reaching out to affected developers to help them address these issues.
Developers, on the other hand, can learn from this and start increasing their security measures to prevent any such misconfigurations. These include following Google’s recommended guidelines in terms of the Firebase database itself and general ones as well such as securing the databases with strong authentication measures & encrypting user passwords.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.