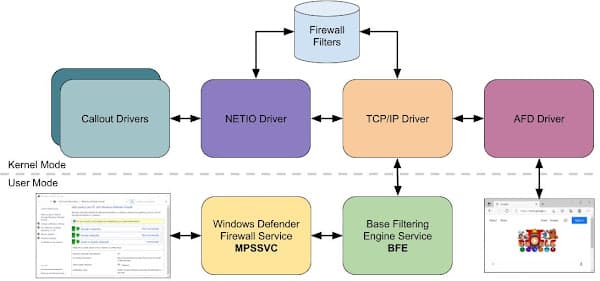
Microsoft was informed about the vulnerability by Google but the company claimed it to be a “non-issue” and that it “will not fix it.”
On Thursday, Google Project Zero researcher James Forshaw shared details of a Windows AppContainer vulnerability after Microsoft backtracked on its previous stance of not fixing the flaw and announcing to address it soon.
In a recent blog post, Forshaw disclosed his findings into the Windows firewall and AppContainer, a sandbox used for testing Windows app security before allowing applications to run on the system.
Forshaw reported his findings to Microsoft on July 8th, 2021, and now published an advisory with proof-of-concept.
It’s Not a Non-issue, after all!!
Initially, Microsoft brushed it off, claiming it to be a “non-issue” and that the company “will not fix it.” On July 18th, 2021 Microsoft told Google researchers this vulnerability could not be exploited without compromising AppContainer; therefore, the company wasn’t bothered about the issue.
SEE: Google reveals details on active vulnerability affecting Windows 10, 7
Microsoft stated that AppContainer was a restrictive execution environment preventing applications running within the environment from accessing other apps, files, hardware, registry, and network resources, which the apps weren’t allowed to access.
In other words, the company stated that apps implemented through AppContainer could not be hacked. But, Forshaw revealed a way to bypass these restrictions and access services on intranet resources and localhost.
“The default rules for the connect layers permit certain executables to connect TCP sockets in AppContainers without capabilities leading to elevation of privilege,” Forshaw wrote in their blog post.
Windows 10 Version 2004 Declared Vulnerable
The Windows vulnerability can cause elevation of privilege (EoP). The issue is that under the Windows Filtering Platform (WFP) rules, it can permit executable files to connect to TCP sockets in AppContainers and enable an attacker to obtain EoP and inject malicious code by connecting to an external network resource via an AppContainer.
“For example, connecting to the internet via IPv4 will process rules in the FWPM_LAYER_ALE_AUTH_CONNECT_V4 layer,” Forshaw explained.
He further revealed that the vulnerability could impact any Windows system, but he specifically mentioned Windows 10 version 2004 in his report. He also stated that the flaw could result in a malicious executable letting an attacker access intranet locations. Project Zero has awarded this vulnerability a low critical rating.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.