Apple paid $75,000 to the hacker for reporting the camera hijacking bugs.
There are two main types of hackers, Black Hat Hackers are the bad guys who perform hacking with malicious objectives, and White Hat Hackers are the good guys. Also referred to as ethical hackers, the white hat hackers help tech firms and organizations improve their security mechanisms by identifying and reporting inherent flaws in their products/services. They do this by using their hacking prowess and in a way they support organizations in protecting their systems and offerings from black hat hackers.
See: Creepy website shows live footage from 73,000 Private Security Cameras
The scope for ethical hacking has expanded tremendously and it has transformed into a lucrative profession. Ryan Pickern, the founder of a proof-of-concept sharing service BugPoC, is the perfect example in this regard. The ex-security engineer at Amazon Web Services, Pickern earned a whopping $75,000 via the Apple Security Bounty program for identifying seven zero-day vulnerabilities in the iPhone camera.
Reportedly, in December 2019, Pickern was inspecting Safari for iOS by hammering the browser with “obscure corner cases” and that’s when he discovered an unusual behavior. When he examined the camera’s “intense” security model closely, he was able to find seven zero-day vulnerabilities out of which three could potentially be used for hijacking the camera.
See: iPhone apps can access cameras to secretly take photos and record videos
As per the details revealed by Pickern, if the user is lured towards an infected video conferencing website, the infected version can obtain direct access to the camera.
“Put simply—the bug tricked Apple into thinking a malicious website was actually a trusted one. It did this by exploiting a series of flaws in how Safari was parsing URIs, managing Web origins, and initializing secure contexts” explained Pickern.
Here’s a preview:
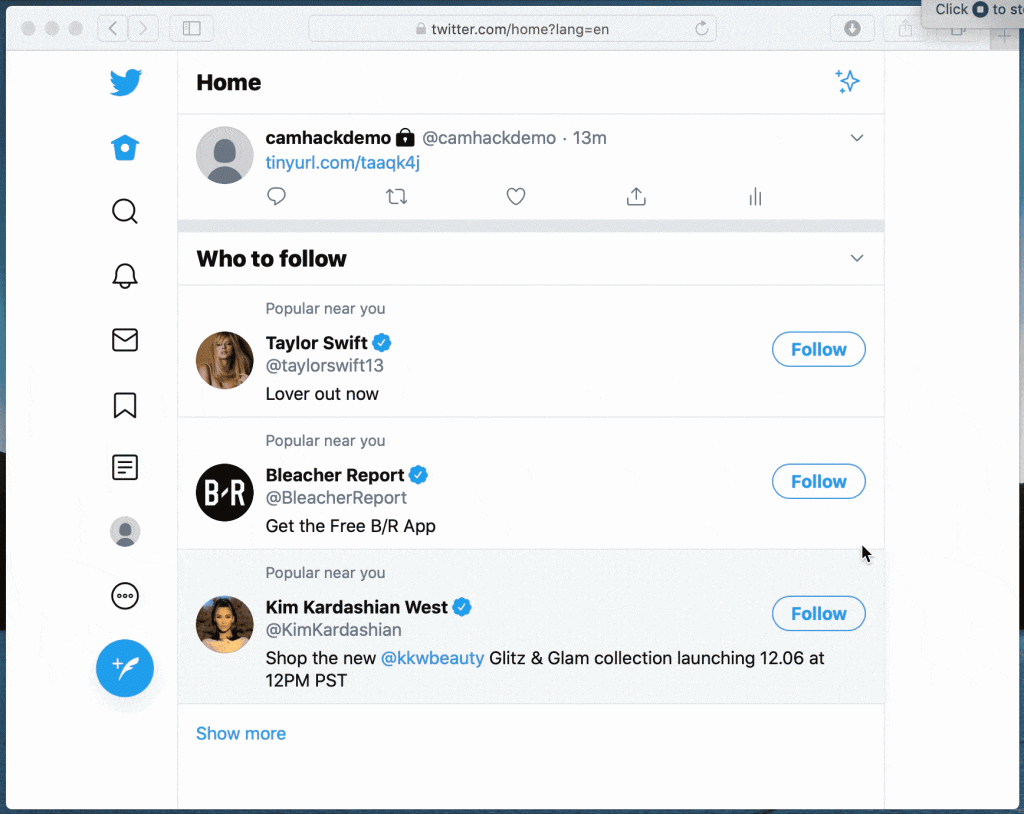
The vulnerabilities were identified in the Webkit browser engine and Safari. When combined together, the flaws would let infected websites to activate cameras on iPhone, iPad, and Mac.
Eventually, Pickern hijacked the iPhone’s camera and notified Apple product security team about it. The company patched the flaws in January and rewarded Pickern with a handsome amount.
See: Vulnerability in Zoom video conference app lets Mac’s camera hijacking
As for Apple’s Security Bounty Program; launched in December last year, the program offers white hack hackers and security research some big bucks. You can also become a part of it. More information on the Security Bounty Program is available here.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.