How to bypass censorship? It’s not as simple as it seems but researchers from the University of Maryland’s Computer Science Department are claiming to have the ultimate solution after all.
It is a fact that millions of people around the world face censorship on the internet especially websites being blocked by ISPs. This is common in authoritarian regimes like China and Saudi Arabia in addition to various 3rd world countries spread across globally.
It may come as a surprise to you (or not) but Google and Facebook are banned in China.
To solve this problem, we usually use VPNs or perhaps if you’re a bit more tech-savvy, the TOR network. However, all of these require conscious efforts on behalf of you the user in which you have to install some extension or another software altogether.
Yet, have you ever imagined an internet where you did not have to do anything and all these blocked websites would “un-block” themselves for you magically?
See: List of Eight Popular websites That are Banned in China
This is exactly what a group of researchers from the University of Maryland’s Computer Science Department have come up with. Dubbed as Geneva; they have made a tool that lets the blocked websites do the effort of evading censorship filters themself without you having to intervene.
How it does so is by tampering with the packets when they are being transmitted from a server outside the country which in essence “confuses the censor” inside the user’s country. This is done using a component called “Strategy Engine.”
Secondly, since different censors operate differently, it deals with this change by employing multiple evasion strategies learned through its algorithm helping it constantly evolve.
During the testing process, the tool was run over 5 different protocols on IPv4 including DNS (over TCP), FTP, HTTP, HTTPS, and SMTP and in 6 countries comprising of Australia, Germany, Ireland, Japan, South Korea, and the United States. This though was on the server-side. The researchers clarify by stating in their report that,
We used unmodified clients within four nation-state censors—China, India, Iran, and Kazakhstan—to connect to our servers. For each nation-state censor, we trained on each protocol for which we were able to trigger censorship; all four countries censored HTTP, but only China censored all five protocols.
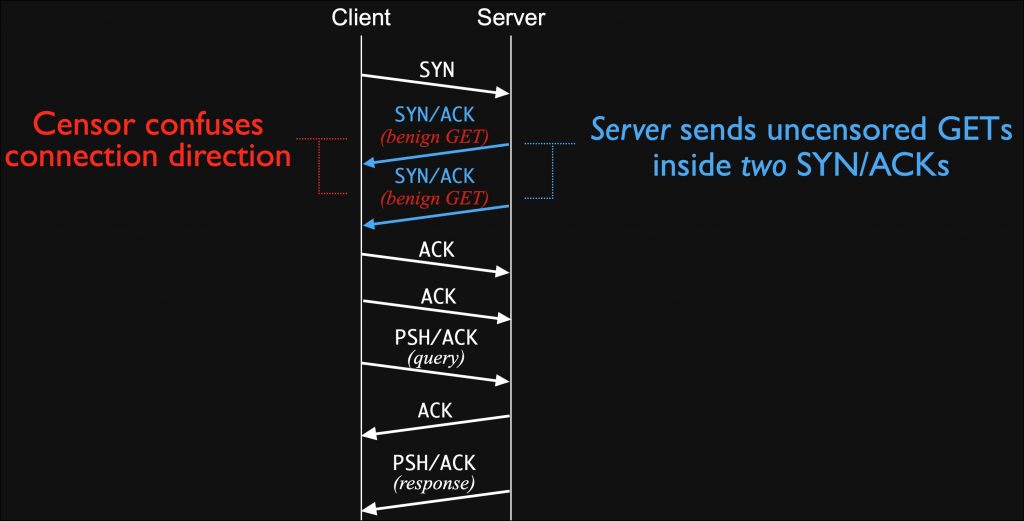
Explaining the strategy above, the researchers state,
During the three-way handshake, instead of sending one SYN/ACK packet like usual, the server sends two SYN/ACK packets. On each packet, it attaches a payload: a well-formed HTTP GET request for some benign resource (GET / HTTP/1.1\r\nHost: example.com\r\n\r\n). This evaded Kazakhstan’s censorship with 100% success rate in our tests.
To conclude, this is something new and can be instrumental in the future fight against censorship. An important thing to remember is that there is no one-fit-all solution and as mentioned above, different tactics will be needed by an evolving algorithm to fight the censorship tactics implemented by governments.
See: Top 10 worst countries for Internet freedom & censorship
Moreover, with the news of this tool spreading, state officials will certainly try to make their way more robust against this tool with a constant struggle in between. As a parting note, the tool is open-source so you can also try it out for yourself on Github.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.









