This report does not highlight threats against iPhones.
Mcafee has released its Mobile Threat Report for 2020 which analyses different sources of attacks against smartphones. These include the usual backdoors, trojan horses, cryptojacking and many more. However, one method which stands out is the use of hidden apps to perform deceptive functions, making up 50% of all malicious activity.
This marks an astonishing 30% increase from 2018 revealing that 2020 will also see a continuing surge.

According to the report , there are a number of ways attackers employ to successfully target users in line with changing trends. Firstly, as smartphone gaming has become more popular (stop facepalming console gamers), it is not surprising that someone will want to take advantage of this.
How it’s done is that the bad guys spread malicious app links in chat windows of gaming messaging platforms and other potential channels. Then even though the app reflects the real one in terms of its functionality, once the user downloads it, it in actuality harvests user data and also shows intruding ads.
A similar technique was exposed when attackers were caught using STEAM chat to spread malware and remote administration tool (RAT). In another attack, STEAM accounts were compromised to spread malicious links through its chat feature.
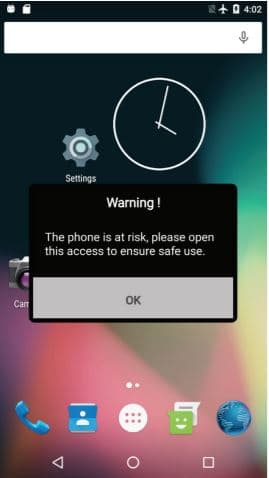
Secondly, a new malware named LeifAccess (also known as Shopper) has been discovered which misuses in-built accessibility features of Android. It does so by harassing users with fake warnings such as “security error should be dealt with immediately” and getting them to grant access to these services which are then used to perform a range of actions such as creating third party accounts.
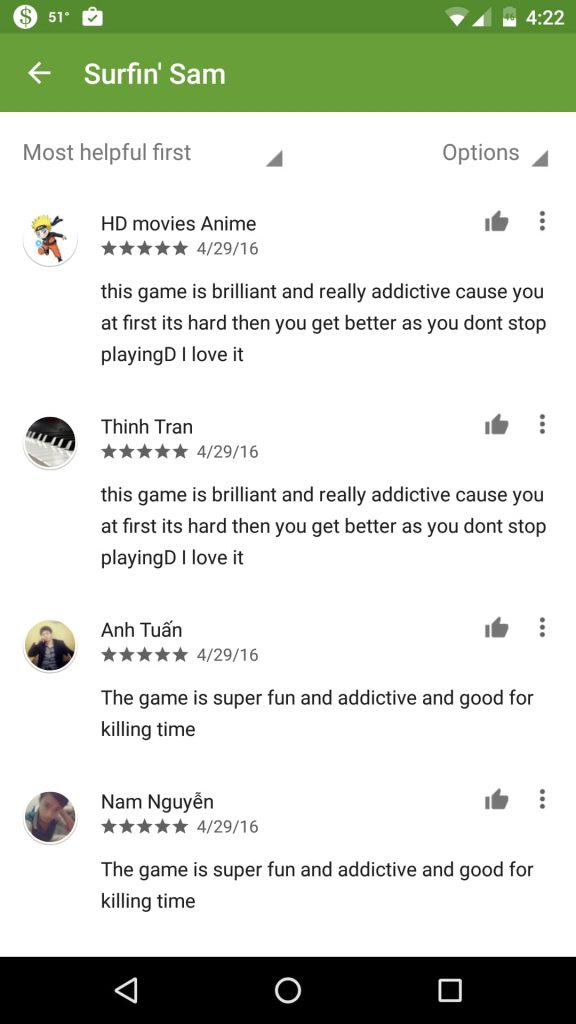
Furthermore, it posts fake reviews on the Play Store in multiple languages in order to make malicious apps appear more legitimate which is somewhat unique. These are though recognizable if one sees beyond just the star ratings since the written reviews are always comprised of generic phrases such as “very simple and useful.”
Nonetheless, even if a user does not grant access to accessibility services, it still continues to install apps and does malvertising. As also seen in previous Android malware, Shopper also does not have its own icon and hence makes it difficult for victims to uninstall it.
Thirdly, instead of creating and distributing their own malicious app, we saw attackers gaining access to legitimate apps and misuse them for their own motives. These include a range of South Korean apps in the transit category infected with a “fake library and plugin that could exfiltrate confidential files called MalBus” as reported by Mcafee in a press release. The data gained from such a compromise include “bus stop locations, route maps, and schedule times for more than 5 years.”
To conclude, we’ve seen certain trends grow over time out of which malicious apps happen to be one. These as observed are further divided into distinct categories showing how complex these attacks have gotten.
Therefore, to protect one’s self from these attacks is no longer possible by only relying on programs such as anti-virus. If attackers are employing social engineering to trick us, it is vital that we respond by taking precautions in real-time while using our human intelligence. An example specific to this case is of vetting real app reviews from automated fake ones as seen above.
Moreover, think – why are all of these reviews similar in terms of their length and also quite simple, far from what humans would write? Something seems fishy and so in this way, such attack vectors can be successfully thwarted.
Furthermore, it is essential that users start sticking to legitimate sources for downloading their apps like Google Play Store and avoid third-party app stores since the majority of malicious apps can be found in the latter.
Did you enjoy reading this article? Kindly do like our page on Facebook and follow us on Twitter.