The BloodyStealer malware is being sold on Russian hacking forums while its capabilities include stealing gaming logs, login credentials, and much more.
On Monday 27th, the IT security researchers at Kaspersky Labs reported a new malware whose prime target is users on gaming platforms like Steam, Epic Games Store, and EA Origin, among others.
BloodyStealer malware
Dubbed BloodyStealer by researchers; the malware is capable of stealing game-related logs, login credentials, and other data from a targeted device.
SEE: Latest LokiBot malware variant distributed as Epic Games installer
The researchers found that the malware also can steal credit card numbers, passwords, forms, and data stored in cookies, in addition to taking screenshots and other activities, relying on an “efficient anti-detection technique.”
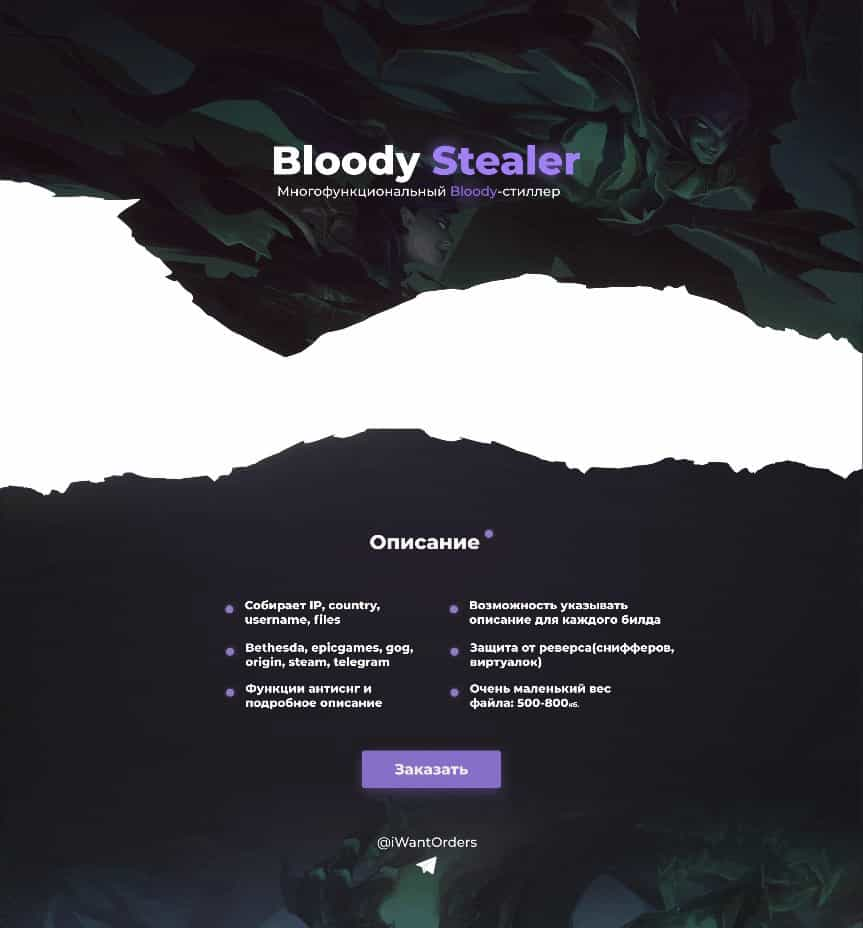
Following is the English translation of the image above in Russian language highlighting the capabilities and features of BloodyStealer:
- Grabber for cookies, passwords, forms, bank cards from browsers
- Stealer for all information about the PC and screenshots
- Steals files from the desktop (.txt) and the uTorrent client
- Collects logs from the memory
- Duplicate logging protection
- Reverse engineering protection
- Not functional in the CIS
- Steals sessions from the following clients: Bethesda, Epic Games, GOG, Origin, Steam, Telegram, VimeWorld.
Malware sold on Russian hacking forums
According to researchers, the malware was originally identified in March 2021 sold on Russian language dark web cybercrime and hacking forums. However, the final sale is carried out on Telegram encrypted messaging service.
As for the price; BloodyStealer’s author is offering a $10 “monthly plan” and $40 for lifetime access.
Although not created exclusively to attack gaming platforms, BloodyStealer appears as one of the weapons of choice for cybercriminals interested in targeting the lucrative gaming platforms, according to the report.
It is worth noting that attacks using BloodyStealer malware have already been detected in Europe, Latin America, and the Asia-Pacific region. In a blog post, researchers warned that,
With its interesting capabilities, such as extraction of browser passwords, cookies, and environment information as well as grabbing information related to online gaming platforms, BloodyStealer provides value in terms of data that can be stolen from gamers and later sold on the darknet.
How to protect yourself from BloodyStealer malware
If you are on gaming platforms it is advised to look out for BloodyStealer malware. You can do that by enabling the two-factor authentication method and block any malicious login attempt to your account.
SEE: How data collected in gaming can be used to breach user privacy
Another important measure is not to click on suspicious links displayed during matches and in messages that lead to external sites. They may redirect gamers to fake login pages where they will be asked for their username and password.
Avoid downloading pirated and third-party software and games as cybercriminals have been spreading all sorts of malware and ransomware infection through pirated software. Nevertheless, it is also advised to scan your device regularly with reliable anti-virus software especially Kaspersky products that detect the threat as Trojan-Spy.MSIL.Stealer.gen.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.